In this year, IP spoofing tools will become more common than ever. This article will cover Rbndr, Fakenetbios, and Synner. Learn how these tools work and how they can protect your network. Then, take action against IP spoofing tools today. There’s no time to protect your network and ensure your information is safe.
In the realm of cybersecurity, IP spoofing is a method used to trick a target by disguising the source of the message. This technique is employed by malefactors to gain illegal entry into a network or system. IP spoofing can be accomplished using various utilities, and in this article, we will discuss the most common IP spoofing tools.
What is IP Spoofing?
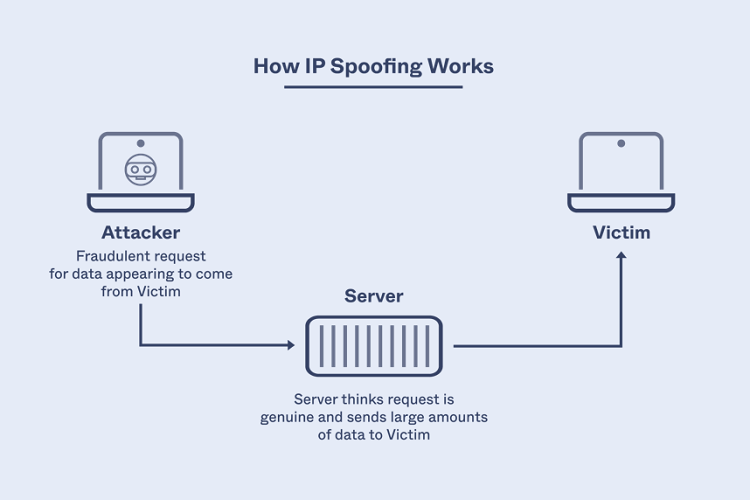
IP spoofing is a vicious act where cybercriminals essay to trick individualities and company workers. They generally copy the identity of an authorized person to gain access to sensitive information like bank details.
In the world of cybersecurity, IP spoofing is a common fashion used by hackers to gain unauthorized access to computers and networks. IP spoofing involves the use of a fake IP address to disguise the bushwhacker’s identity and position, making it delicate to trace the source of the attack.
IP address spoofing, you should know that the internet sends and receives data through small packets that store the source information.
An IP spoofer alters the original address with a caricature IP address.
Another IP spoofing system uses thousands of bias to shoot dispatches to multiple donors( generally a vast number) using the same spoofing IP address. As similar, the entering system subventions the authorization and cataracts the targeted garçon.
How to Stop Email Spoofing?
Know how to stop email spoofing and defend your company from assaults with this article.
- Packet Filtering
This process principally analyses the title of every packet to confirm if the IP address matches with the source. The computer doesn’t let the packet complete the route in case of any disagreement.
- Authenticating druggies and bias Through PKI
Public key infrastructure (PKI) is an authentication system grounded on public and private crucial dyads. The private crucial encrypts the communication, and the public key does the contrary.
So, the asymmetric crucial system is used, which means that both public and private keys are distinguishable. As similar, IP spoofers are unfit to determine the private key. This system has proven to be largely effective in precluding man-in-the-middle IP spoofing.
Most Common IP Spoofing Tools
In this composition, we will bandy the most common IP spoofing tools used by hackers and how to help them.
1. Synner
The Most Common IP Spoofing tools will be RUDY, libpcap, Aranea, and snoop. These tools will allow you to sniff traffic, hide your identity, and perform a range of other malicious activities on your network. RUDY, for instance, is designed to sniff the traffic of a network and determine the protocol that a particular packet uses. Aranea has multi-threaded capabilities and is a popular choice for IP Spoofing on a network.
Fakenetbios is an IP spoofing tool that aims to emulate Windows hosts on a LAN. It comes in two variants: DGM and Ns. DGM sends Netbios diagram service packets on port UDP 138, and Ns listens for Netbios name requests on port 137. It’s a fast and easy way to test your software for vulnerabilities, as it doesn’t require a server. On the other hand, Ns responds to Netbios name requests, just like a real Windows computer.
Another solution to prevent IP spoofing attacks is network filtering. This will block packets with suspicious source addresses. Authentication is also another great way to prevent spoofed traffic. Network administrators can configure their routers and switches to reject incoming packets. They can also use alert-based traffic monitoring to block spoofed and bad traffic. This solution can help protect your network from DDoS attacks depending on the threat.
2. Fakenetbios
There are numerous uses for IP spoofing tools across the web, including identity theft. But what are the dangers of IP spoofing? Bad actors will do anything to steal someone else’s identity, which is why “IP spoofing” is so attractive to them. It’s one of the easiest ways to steal someone else’s personal information, so users must stay vigilant and protect their online identities.
IP spoofing bypasses firewalls, and other security measures that block connections from untrusted IPs. While most companies discourage using IP authorization, IP spoofing makes it much harder for these security measures to work. Instead, companies encourage users to use other methods to verify their identity, including biometrics, such as a username and password.
Fakenetbios is a tool used to spoof NetBIOS responses. It can be utilized to conduct IP spoofing attacks by spoofing NetBIOS responses and tricking a target system into sending traffic to a spoofed IP address. Fakenetbios can be utilized to bypass security controls and gain unauthorized access to a network.
Fortunately, several tools have been developed to circumvent these protections. One such tool, Fragroute, can intercept and modify traffic on a network. This open-source tool has a command line interface and works on Linux, BSD, and Mac OS. To understand more about this tool, visit Shodan, an online database of IP address-to-device mappings.
3. Rbndr
A common type of IP spoofing tool is Fakenetbios. Fakenetbios is a software program that simulates Windows hosts on a local area network. There are two main types of Fakenetbios: the DGM and the Ns. The DGM sends Netbios diagram service packets on port UDP 138, and Ns listens on port 137 and responds to Netbios name requests like a real Windows computer would.
The main function of rbndr is to test the vulnerability of DNS rebinding software. It randomly picks an address from a hostname. It is a very simple tool because it does not require a server. However, it may give you access to any IP address. This tool has legitimate uses across the web. Therefore, you must protect yourself from it and implement proper mitigations.
While traditional security measures will detect attacks on secure systems, IP spoofing will allow hackers to remain undetected for a long. By assuming the identity of a trusted source, hackers can access the system and do more damage before a security team can take action.
4. Nmap
Nmap (Network Mapper) is an open-source tool designed for network discovery and security auditing. It allows users to discover hosts and services on a network, which can be instrumental in identifying potential targets for IP spoofing. With its versatile command-line interface and graphical user interface, Nmap can perform a variety of scans, including TCP, UDP, and SYN scans, making it a favorite among network administrators and security professionals alike.
Beyond simple discovery, Nmap’s scripting engine (NSE) enables users to write scripts to automate a range of networking tasks, including vulnerability detection and exploitation. Its ability to provide detailed information about the operating systems and services running on remote devices makes it a valuable asset for those seeking to spoof IP addresses, as it helps in crafting targeted attacks while minimizing exposure to detection.
5. Hping
Hping is a command-line oriented TCP/IP packet assembler and analyzer, often used for network testing and security auditing. It is particularly useful for crafting custom packets and manipulating various TCP/IP protocol fields, making it a powerful tool for IP spoofing. Hping can perform a variety of tests, including TCP, UDP, ICMP, and RAW IP, allowing users to simulate different types of network traffic and assess the response of the target system.
One of Hping’s notable features is its ability to create complex packet sequences, enabling users to configure the source IP address, port, and other parameters. This flexibility allows for sophisticated testing of firewall rules and intrusion detection systems, providing valuable insights into the effectiveness of security measures. As a result, Hping is favored by penetration testers and network engineers for its robust capabilities in exploring network vulnerabilities.
6. Scapy
Scapy is a powerful Python-based interactive packet manipulation tool and library that enables users to create, modify, and send network packets with ease. Its high-level interface allows for the crafting of custom packets, making it an excellent choice for IP spoofing. Scapy supports a wide range of protocols, including Ethernet, IP, TCP, and UDP, allowing users to manipulate packet fields and conduct comprehensive network analysis.
What sets Scapy apart is its ability to handle complex tasks such as network discovery, packet sniffing, and even network attacks. With its extensive library of built-in functions, users can automate tasks and create scripts for specific network scenarios. This versatility makes Scapy a favorite among security researchers and ethical hackers looking to explore and exploit vulnerabilities within network infrastructures.
7. Metasploit
Metasploit is a comprehensive penetration testing framework that provides security professionals with the tools needed to exploit vulnerabilities in networks and applications. It includes a suite of exploits, payloads, and auxiliary modules that can be leveraged for IP spoofing and various types of attacks. Metasploit’s powerful capabilities allow users to simulate real-world attacks to assess the security posture of their systems.
One of the key features of Metasploit is its Metasploit Community, which provides a platform for collaboration and sharing of exploits and methodologies. The framework also integrates with various other tools and platforms, enhancing its functionality. As a leading tool in the realm of penetration testing, Metasploit empowers users to conduct thorough security assessments and develop strategies to mitigate potential risks.
8. Cain and Abel
Cain and Abel is a versatile password recovery tool for Microsoft operating systems, but it also includes features for network sniffing and IP spoofing. It allows users to capture and analyze network traffic, making it easier to identify vulnerabilities and perform man-in-the-middle attacks. With its user-friendly interface, Cain and Abel is accessible to both novice and experienced users, making it a popular choice for network security testing.
In addition to its password recovery capabilities, Cain and Abel can be used to perform ARP poisoning, which can facilitate IP spoofing. Its ability to analyze encrypted protocols and recover passwords from various sources adds to its appeal as a comprehensive security tool. As a result, it remains a staple in the toolkit of many security professionals looking to test and enhance network defenses.
9. Zestproxy
Zestproxy is a powerful web proxy tool designed for testing and debugging web applications. It intercepts and modifies HTTP and HTTPS traffic, allowing users to analyze requests and responses in real time. This capability is particularly useful for IP spoofing, as it enables users to manipulate headers and simulate traffic from different IP addresses, thereby testing how applications respond to varying network conditions.
What makes Zestproxy stand out is its user-friendly interface and robust feature set, including support for multiple protocols and the ability to record and replay HTTP sessions. These features make it an essential tool for web developers and security testers looking to identify vulnerabilities in their applications. By facilitating in-depth analysis of web traffic, Zestproxy empowers users to enhance the security and performance of their web applications.
10. Mitmproxy
Mitmproxy is an interactive, SSL-capable man-in-the-middle proxy that allows users to intercept, inspect, and modify network traffic. It is particularly effective for testing and debugging web applications, and its ability to perform IP spoofing makes it a valuable tool for security researchers. Mitmproxy supports various protocols, including HTTP, HTTPS, WebSocket, and TCP, providing extensive capabilities for traffic manipulation.
One of the key features of Mitmproxy is its command-line interface and scripting capabilities, which enable users to automate tasks and customize their testing environments. Its user-friendly interface allows for real-time inspection and modification of requests and responses, making it easier to identify potential vulnerabilities. As a result, Mitmproxy is widely used by developers and security professionals seeking to ensure the integrity and security of their applications.
11. Wireshark
Wireshark is a widely used network protocol analyzer that provides detailed insights into network traffic and operations. This powerful tool captures and displays data packets in real time, allowing users to analyze the flow of information across a network. While not specifically designed for IP spoofing, Wireshark’s capabilities make it an essential tool for identifying and diagnosing network issues, as well as monitoring for suspicious activity.
With its extensive filtering options and ability to decode numerous protocols, Wireshark enables users to inspect packet contents and understand the underlying network behavior. Security professionals often use Wireshark to monitor network traffic for signs of potential IP spoofing or other malicious activities, making it an invaluable asset in the toolkit of anyone concerned with network security.
12. Sslstrip
Sslstrip is a tool that allows attackers to transparently hijack HTTPS connections, effectively downgrading them to HTTP. This capability makes it possible to intercept and manipulate sensitive data transmitted over supposedly secure connections. While primarily associated with man-in-the-middle attacks, Sslstrip can also play a role in IP spoofing by enabling attackers to masquerade as legitimate servers, tricking users into sending sensitive information.
One of the notable features of Sslstrip is its ability to rewrite URLs on-the-fly, ensuring that users are directed to the HTTP version of a site rather than the secure HTTPS version. This functionality allows attackers to capture unencrypted data, making Sslstrip a powerful tool for those seeking to exploit vulnerabilities in web security. As a result, it serves as a reminder of the importance of robust security practices in safeguarding against such attacks.
13. Burp Suite
Burp Suite is a comprehensive web application security testing framework that offers a range of tools for assessing and exploiting vulnerabilities. Its proxy server allows users to intercept and modify HTTP/S traffic, making it a valuable tool for IP spoofing. Security professionals use Burp Suite to perform penetration tests, identify weaknesses in applications, and validate security measures in place.
Burp Suite’s extensibility through plugins and its user-friendly interface make it accessible to both beginners and advanced users alike. The suite includes features such as a scanner, intruder, and repeater, which help automate the testing process and streamline the identification of vulnerabilities. As a leading choice for web security testing, Burp Suite empowers users to enhance the resilience of their applications against potential threats.
14. Arpspoof
Arpspoof is a tool that allows users to perform ARP (Address Resolution Protocol) spoofing attacks on a network. By sending forged ARP messages, it can associate the attacker’s MAC address with the IP address of another device, effectively redirecting traffic meant for that device to the attacker. This capability makes Arpspoof a popular choice for security professionals and ethical hackers looking to test network security.
The simplicity of Arpspoof, combined with its effectiveness, makes it a go-to tool for those looking to demonstrate the vulnerabilities associated with ARP. It is often used in conjunction with other tools to create comprehensive security assessments. As a result, Arpspoof serves as a reminder of the importance of securing local area networks against such attacks.
15. Nbnspoof
Nbnspoof is a lesser-known tool that allows users to spoof their Network Block Number (NBN) address. This tool can be helpful for testing network configurations or for privacy purposes, as it enables users to mask their true network identity. Nbnspoof is particularly useful for telecom professionals and security researchers who seek to understand the implications of network address manipulation and its impact on service delivery.
While Nbnspoof may not be as widely recognized as other tools, its functionality can provide valuable insights into network behavior and security. By allowing users to experiment with different configurations, Nbnspoof aids in the development of effective strategies for managing network resources and addressing potential vulnerabilities.
16. Netcommander
Netcommander is a network management tool that provides users with various functionalities for monitoring and configuring network devices. While it is not specifically designed for IP spoofing, its capabilities in analyzing network traffic and managing devices make it a useful tool for administrators seeking to secure their networks. Netcommander’s intuitive interface allows users to manage IP addresses and monitor network performance effectively.
Security professionals can leverage Netcommander’s features to identify potential vulnerabilities and optimize network configurations. By providing insights into network traffic patterns and device statuses, Netcommander assists in the ongoing effort to maintain robust network security and prevent unauthorized access. Its versatility makes it a valuable asset in any network management strategy.
17. Aranea
Aranea is a sophisticated network security tool that specializes in spoofing IP addresses and conducting penetration tests. Designed for security professionals and ethical hackers, Aranea allows users to craft and manipulate packets with precision, enabling them to simulate various network scenarios. Its user-friendly interface makes it accessible for both beginners and experienced users, facilitating the exploration of IP spoofing techniques without extensive technical knowledge.
What sets Aranea apart is its ability to seamlessly integrate with other network analysis tools, amplifying its effectiveness in identifying and exploiting vulnerabilities. By providing comprehensive features for packet crafting and analysis, Aranea empowers users to conduct thorough assessments of network defenses. As a result, it has gained recognition as one of the best tools for IP spoofing, contributing significantly to the field of network security and ethical hacking.
Why is IP Burlesquing Dangerous?
IP spoofing can put the image of your company in jeopardy and effects can get worse if the hackers target your guests by stealing their information from your database. It’s extremely delicate to identify a caricature IP. Before your system knows, the detriment is done. Then are the three reasons that make it challenging to detect an IP caricature.
- Precluding IP Burlesquing
To help IP spoofing, it’s important to apply strong security measures, similar as packet filtering and firewalls. Packet filtering involves examining incoming and gregarious packets and blocking those that are suspicious or have a fake IP address. Firewalls can also be used to block incoming business from known vicious IP addresses. In addition, it’s important to keep software and operating systems up to date with the rearmost security patches. This can help help vulnerabilities that can be exploited byhackers.
Conclusion
In conclusion, IP spoofing is a severe threat to network security. Attackers use IP spoofing to gain unauthorized access to a network or system. There are many tools available to conduct IP spoofing attacks, and
it’s essential for network administrators and security professionals to be aware of these tools and how they are used.
IP spoofing is a common fashion used by hackers to gain unauthorized access to computers and networks. By understanding the most common IP spoofing tools used by hackers and enforcing strong security measures, individualities and associations can cover themselves from these types of attacks.
By understanding the tools and techniques used by attackers, network security can be improved, and vulnerabilities can be identified and addressed before they are exploited. It’s also crucial to implement security best practices, such as using strong passwords, keeping systems and software up to date, and implementing firewalls and other security controls, to minimize the risk of IP spoofing attacks. With the right tools and practices, organizations can better protect themselves from IP spoofing and other cyber threats and beyond.



