Cybersecurity is a common concern for every company on the planet whether they’re remote or in office. Data breaches and hacks can happen to any company that doesn’t put cybersecurity at the top of their list. It’s a common saying that there are two companies in the world; those who know they have been hacked and those who don’t. To this day, many companies still only rely on username and passwords as a way to protect their company assets and have lost millions due to the lack of cybersecurity in their corporation. Fortunately, using Citrix two-factor authentication paired with an authenticator app, users will never have to worry about their information being compromised.
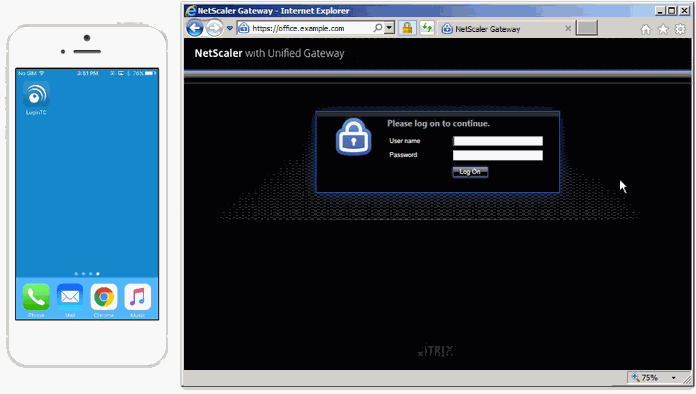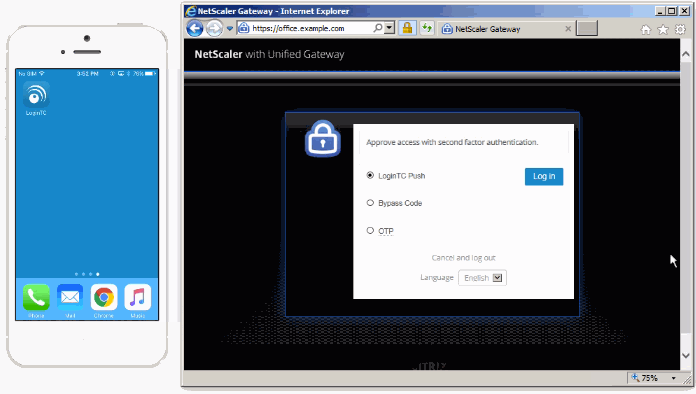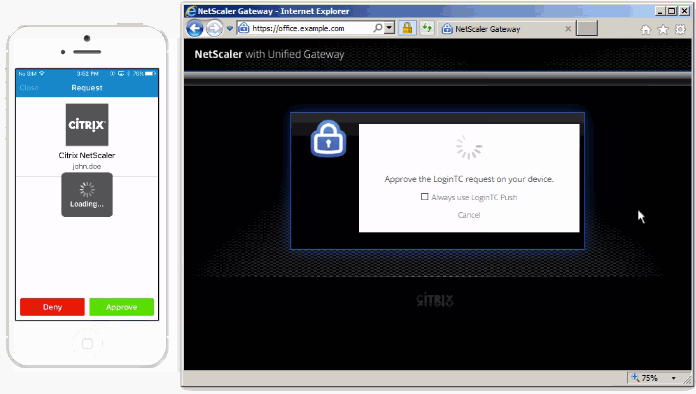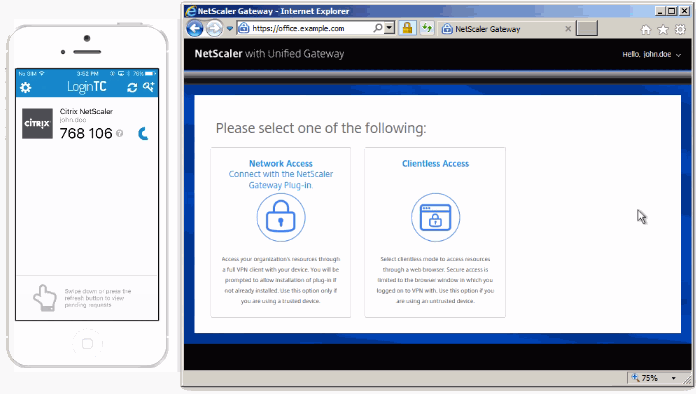
When it comes to protecting your network access security, there’s more options today than there was a few years ago. Organizations today are able to choose between three types of solutions that offer a different level of protection. Let’s take a dive into each type of authentication and how secure they are.
- One-Factor: Something the user knows, typically a password.
- Two-Factor: Something the user knows and something the user has (a token, card, fingerprint, phone).
- Multifactor: Multifactor authentication uses multiple factors to validate the users’ identity. Authentication factors may include items such as location, network, time of day, session ID, device, or even biometric factors such as fingerprints and retinal scans.
With one-factor authentication, the use of password and PINs have been the bulk of security for decades. But the faults of one-factor authentication are becoming better known and more costly to businesses. One factor authentication solutions, such as password protection, clearly are not fully successful when trying to protect everything. Cybercriminals are consistently increasing their game and passing through one-factor systems easily.
When you use two-factor authentication, you are providing a more effective defense against security threats than one-factor authentication solutions. There are many ways to deploy 2FA solutions but oftentimes they can prove to be difficult for users to use when trying to log in to their accounts – use of hardware tokens specifically. The need for an authentication solution that can foil cybercriminals without frustrating the users is fairly urgent. Citrix two-factor authentication, paired with an authenticator app, will give your company the best two-factor authentication protection you could ask for.
Multi-factor authentication consists of an authentication method that is more than your typical 2FA method. This could include using biometric authentication such as facial or fingerprint recognition. Multi-factor authentication could also include the use of an outside authenticator as well.
When considering which type of authentication you want to use for your organization, you’ll want to consider the following:
- Security: The type of authentication you choose, must offer an effective security against a wide range of modern, escalating security threats.
- Productivity: You want to choose an authentication solution that can enhance user productivity while not compromising security.
- User Experience: Authentication solutions that provide a level of convenience and eliminate user resistance are generally more accepted across the company. Solutions that offer contextual intelligence capabilities further enhance the user experience by adjusting the level of authentication needed in response to threat level assessments.
- Lower Cost: Choosing an authentication solution that can lower your total cost, while boosting user productivity and strengthens organization security is very realistic.
- Hassle-Free Administration: A multifactor solution should enable faster and easier administration by eliminating common administrative chores such as user enrollment and maintenance.
- Flexibility & Reliability: An authentication method that provides a range of security token delivery options (SMS, email, app, etc.) prove to be the best solutions to maximize reliability and flexibility within your company.
Choosing the appropriate level of security authentication requires evaluating your company and how vulnerable you are to data breaches. More often than not, the level of risk a department could face in terms of a breach, will determine the level of authentication implemented. Using your Citrix two-factor authentication with an authenticator application, not only protects your company’s information but also doesn’t compromise usability, making it easy for your users to authenticate and carry on with their work day. Whether you choose one-factor, two-factor, or multi-factor authentication, you will be able to add Citrix authentication to your log-in to ensure maximum security.