Most of the common types of cyber security threats that are ruined your enterprise suddenly. Identifying cyber attacks is essential for prevention.
The internet is one place where the people across the globe seek resort- to connect to their friends and family, to find answers to their queries, to share information, to perform transactions and most importantly to work. Any modern lifestyle is not void of usage of the internet, so much so that it has not only occupied our personal lives but has also taken over the way we work and do business.
Especially in the era of remote working and enterprise mobility, the devices, the data and the users are out of the protective supervision and secure network of a conventional office, the cyber security is truly at stake. With the help of a mobile device management solution, the enterprise IT teams might be able to keep the security intact to a large extent but it needs the support of employees and the users to do so.
As we become more and more cyber-savvy and tech-reliant, it is also important to understand that the internet is not a safe space. Especially when ignored and undermined, the lurkers behind the shadow of the internet are preying upon our privacy and security. Hence, it is extremely crucial to understand the cyber security threats and how they can negatively impact our digital well-being, our personal data as well as the corporate data that we work with. It is very crucial to protect your data against cyber threats. Taking up an IT Cyber Security certification course which will help you to protect yourself from dangerous Cyber attacks.
In this article, we will learn about the different types of cyber security threats.
What are cyber security threats and attacks: An overview
The term cyber security threat is commonly heard and most likely it is mistaken to be a full-blown attack to a server or password hacking to our emails and other services. Sadly, these are just the tip of an iceberg and there are multiple types of cyber security threats that we can fall prey to. Cyber security threat is essentially a malicious activity that intends to damage your data, steal it and use it without your permission and create a disruption in your online and offline life.
The term cyber security dates back to the 1970s where a researcher named Bob Thomas created a computer program on the ARPANET (The Advanced Research Projects Agency Network) that left a small trail while traveling across the network. Further developed and elevated, this was truly the beginning of the understanding around cyber security.
The real cyber security threats however started in the 2010s, where the use of digital devices- computers, smartphones and the internet was exponentially increasing. Major databases were illegally released, networks with thousands of users were hacked into and cyber security threats became a true concern for everyone who had any type of digital presence.
Cyber security threats can hamper military operations, financial systems, manufacturing and other industries, public transportation, aviation, government agencies, the energy industry, healthcare as well as consumer devices and personal data via connected and IoT devices.
Types of Cyber Security Threats and Attacks
These attackers may or may not be driven by motivation, but we can keep them at the bay if we are well-aware of their possible activities. Let us understand the different types of cyber security threats:
Malware
Malware is a software that performs ‘malicious’ activities on the targeted device or a network. Malware is one of the most common cyber security threats and can walk into your device or system from a website that you just browsed, an app you just downloaded or even a text message that you just opened.
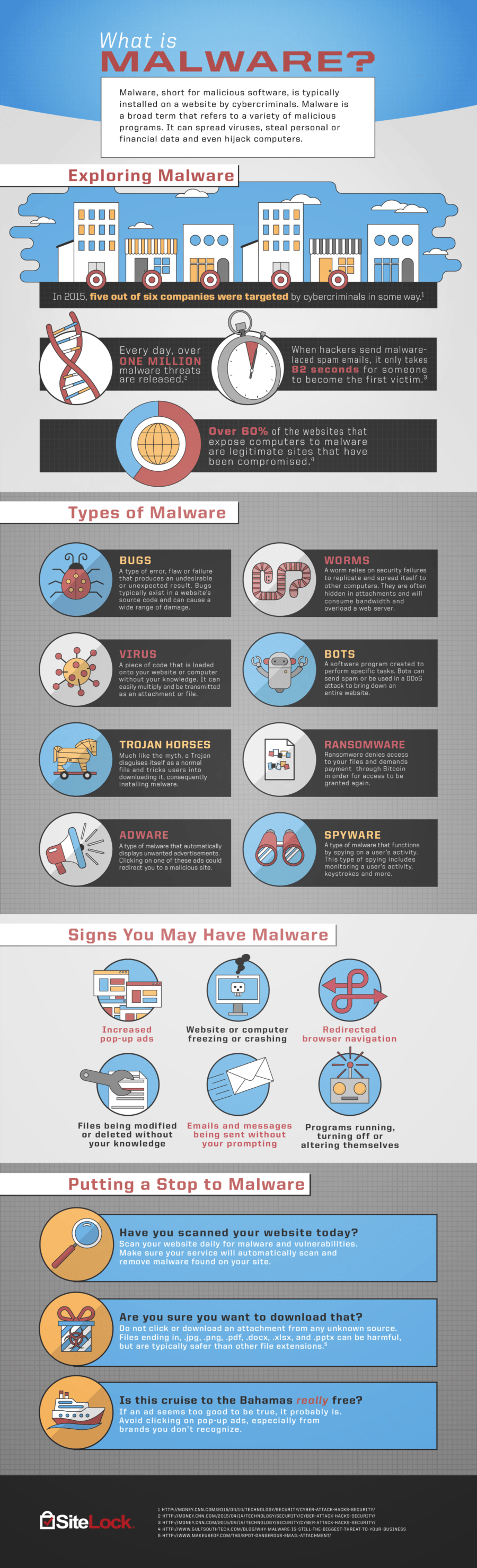
Malware is a guest you do not want in your home but there’s only a little you can do about it once they are in!
Phishing
Phishing contributes to one of the most impactful cyber security threats and attacks of today. Phishing happens through targeted digital messages- most commonly emails that are deceiving, making users open them or even click on the action items where malware is transmitted to the users’ device.
Although most employees as well as users are aware of phishing attacks and the email security seems to be increasing where the user is warned about the email containing malicious links, they still walk into your inbox in the disguise of offers, fake news and more. The phishing threats can result in the users losing access to their own accounts, compromised passwords or even access to credit cards and other financial information.
The more sophisticated and new version of phishing is when the attacker understands the user and knows a lot about their personal choices and creates a personalized email or a message that a user is tempted to open- because it looks authentic! This type of phishing is also known as spear phishing.
Ransomware
Ransomware threats encrypt data on the targeted network or a system and ask for a ransom in exchange for returning it. It is exactly like a kidnapper asking for ransom in exchange for hostages, wherein this case, the hostage is an entire database, a system or a network.
For large companies, financial institutions or sensitive operations, this access is worth gold and can cause serious implications. HNIs are also repeatedly targeted with ransomware.
Backdoor threats
These threats really come from the backdoor. This backdoor can be in a device, a computer system, software or an algorithm. This attack happens via the attacker who bypasses any authentication or control that the device or algorithm security system has in place. The backdoor threats can enter by identifying the vulnerabilities in the system or by taking unauthorized access via a third-party. Backdoor threats happen in secrecy and most often go undetected until a big implication occurs.
It is like someone staying in your home without your knowledge and permission and only acting on it when needed.
Trojans
Remember the greek legend of Trojan- the wooden horse that entered the boundaries of Troy with an army to rescue Helen? Trojans in cybersecurity mean the exact same thing, they enter your device or network looking like something else, only revealing their real identity after they are in. In this case, they walk in as a seemingly harmless software or an app and once in, they let out malicious code or malware.
Direct-access threats
These threats come into the picture when an attacker or any other unauthorized person gains direct access to a device, a network or a database. The unauthorized user gains physical access to a computer or a database can directly copy the contents of the drive or data causing a data breach. These attackers might also compromise the security further by modifying the device settings, OS-level changes, installing malware or any other app.
They might be able to create permanent backdoor access to the device or database and can control the attacked device from a remote location.
D-O-S threat
D-O-S threat or denial to service attack is when the attacker takes control of a network or service and makes it unavailable to its users. These attacks generally attack individual victims by intentionally entering a wrong password multiple times until they are locked out of the service. Sometimes, the attacks block users from a single IP address. These threats cause a hindrance to the users trying to access service while also burdening the service provider network with two many simultaneous requests they might not be capable of handling.
Eavesdropping
Devices, apps and attackers eavesdrop- yes, they do! Our devices and apps eavesdrop to our conversations, especially when they have access to the microphone and speaker of the device. These threats are increasing rapidly, thanks to the IoT powered devices- from smart homes to connected cars.
Eavesdropping is one of the common cyber security threats that employees are asked to look out for when working remotely.
Man in the middle
Electronic messages are so commonly and mindlessly exchanged, little do we know that there could be a man in the middle (MitM) who is intercepting the messages between the sender and the receiver without them knowing. This attack is extremely serious for military operations and can cause confusion as well as serious havoc.
IoT threats
IoT devices today comprise a large number of devices and systems that run several operations- from businesses to industries. These IoT devices are connected to the network as well as the database and are under a constant threat of cyber security attack, especially since they are largely distributed across geographies and might not necessarily have a management system to keep them up to date.
Spoofing
This type of cyber security threat gains access under false pretense. By pretending to be a valid entity to gain access to data, network or systems, the attacker walks in via email spoofing, IP address spoofing, Media access control spoofing or even biometric spoofing where the attacker reproduces fake biometric samples to gain access.
Closing lines
Cyber security threats will continue to grow and evolve as our security systems do. It is important to be aware of the predators, build a culture of security and nurture the best practices for keeping the web a safe place for us and our data.



