If you show an interest in knowing about communication protocols, read this article. This article will give you an overview of the most common types of communication protocols and their differences. You will learn about the SMTP protocol, HTTPS protocol, Common Industrial Protocol (CIP), and SNMP protocol. In addition, you’ll learn about what each type of protocol is used for. Once you understand how these different protocols work, you’ll be ready to use them in your environment.
SNMP protocol
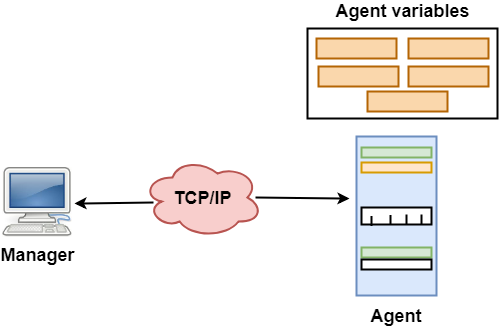
The SNMP protocol is a network management protocol. It uses the concept of a management information base or MIB. MIBs are formal descriptions of a network device’s components and status information. SNMP supports various network devices, including IP video cameras, industrial equipment, and medical devices. SNMP can also monitor services such as Dynamic Host Configuration Protocol.
Although SNMP applies to any size network, it is most useful for large networks. Its architecture allows a network administrator to monitor and manage SNMP devices through a single interface. A network administrator can issue a Set Request to handle a particular machine and a GetNext Request to find the next record in the MIB hierarchy. A GetBulk Request is another SNMP command that can be sent to a large number of agents to gather data.
SMTP protocol
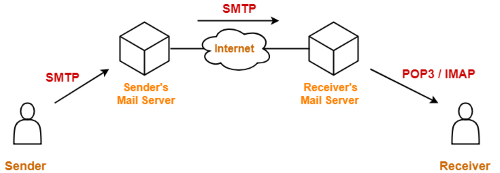
SMTP is an email communication protocol that provides a standard set of codes to simplify sending and receiving messages. It is a standard that enables an email server to reliably reach recipients’ inboxes when messages are sent and received. SMTP was developed by several people, including Jon Postel, Eric Allman, Dave Crocker, Ned Freed, and Keith Moore.
SMTP supports different kinds of message exchange. The sending side uses an MTA (Message Transfer Agent) to prepare the message envelope for transmission. The receiving side uses an MTA (Mail Transport Agent). It must deliver the message and report failures to ensure it reaches its destination. It is impossible to provide a statement if the receiving side cannot process it. However, the receiving side can send messages using an SMTP server that supports relaying.
HTTPS protocol
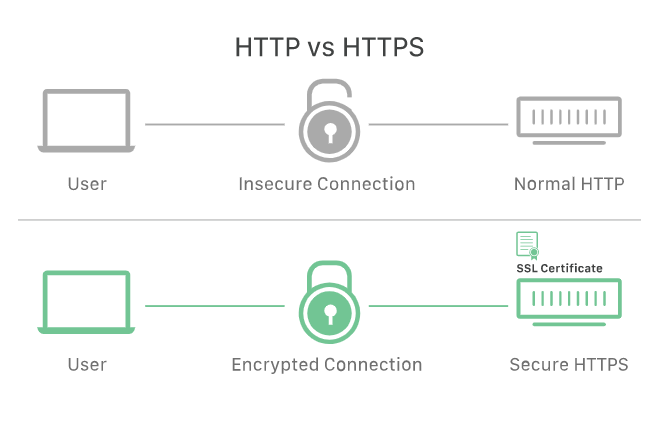
The HTTPS protocol is a telecommunication standard that enables secure data transfer from one computer to another. HTTP uses a protocol known as Secure Sockets Layer to encrypt data before it travels over the Internet. This method prevents data from being intercepted by a third party. This technology was developed to protect against cyber-attacks and other security risks. To learn more about the security of HTTPS, read this article.
HTTPS is a vital component of the Internet and is an important factor in protecting user data. Encryption ensures that sensitive information cannot be eavesdropped on or modified by a third party. HTTPS is also useful in preventing man-in-the-middle attacks, manipulating data, and impersonating a computer on an unencrypted network. It also boosts SEO, as encrypting data makes it easier for search engines to index a website.
Common Industrial Protocol (CIP) protocol
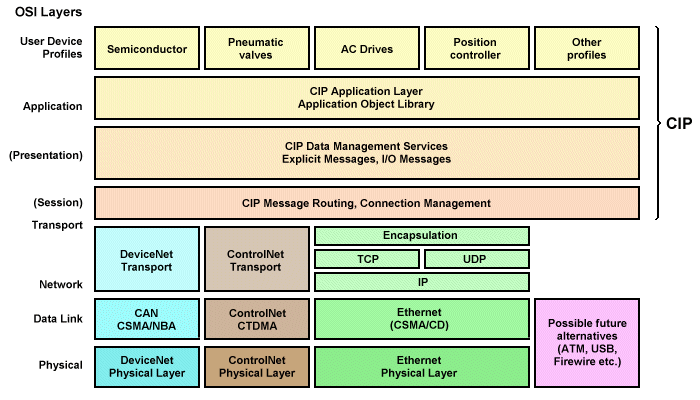
The Common Industrial Protocol, or CIP, is used for industrial automation. It is supported by the ODVA, the Open Data and Vision Association. Common Industrial Protocol is used in factories to send data between devices, such as a weighing scale or a gantry crane. Its popularity has grown, and many companies and manufacturers use it to communicate with one another. Here is a compilation of three reasons why you should use the CIP protocol:
The Common Industrial Protocol defines the types of devices communicating with each other. A CIP device profile specifies each class’s kinds of CIP objects, configuration options, and I/O data. The CIP protocol has a common application interface for devices of the same type, so messages can be sent and received seamlessly. The CIP specification is based on a producer-consumer communication model, which means that many receiving devices can communicate with one another.
TCP protocol
The TCP protocol is a standard for sending data across a network. The protocol uses two main types of headers: a sequence number and a data header. The latter is used to identify the data packet. The TCP header contains ten mandatory fields and an optional extension field. The data section follows the segment header, which carries payload data for the application. The data section length is not specified in the TCP protocol, but it can be determined by subtracting the total length of the IP datagram from the combined size of the segment header and IP header. The TCP pseudo-header contains additional information, such as an SYN flag and the length of TCP headers and payloads.
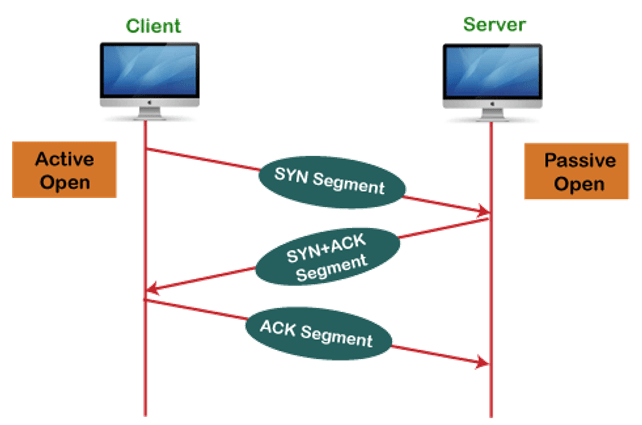
A connection is established between the two TCP servers. This is called the connection establishment phase. The link is found through a multi-step handshake process. The server must be passively open for connection requests. The three-way handshake adds reliability and latency. Another protocol is the User Datagram Protocol (UDP), which provides connectionless datagram services to reduce latency. Both protocols share many characteristics, but each has strengths and weaknesses.



